
A breakdown of the performance of AntiVirus over the past year, based on the Real World Protection Test results from
AV-Comparatives
The top 5 have been marked in green in each image, and the baseline of Microsoft AV is selected in each for comparison.
I have broken it down into how often each package from the monthly top 5 features in the top 5, and how many times a package from this group has the worst hit rate for false positives (marked with *).
First the 2 half year aggregate results.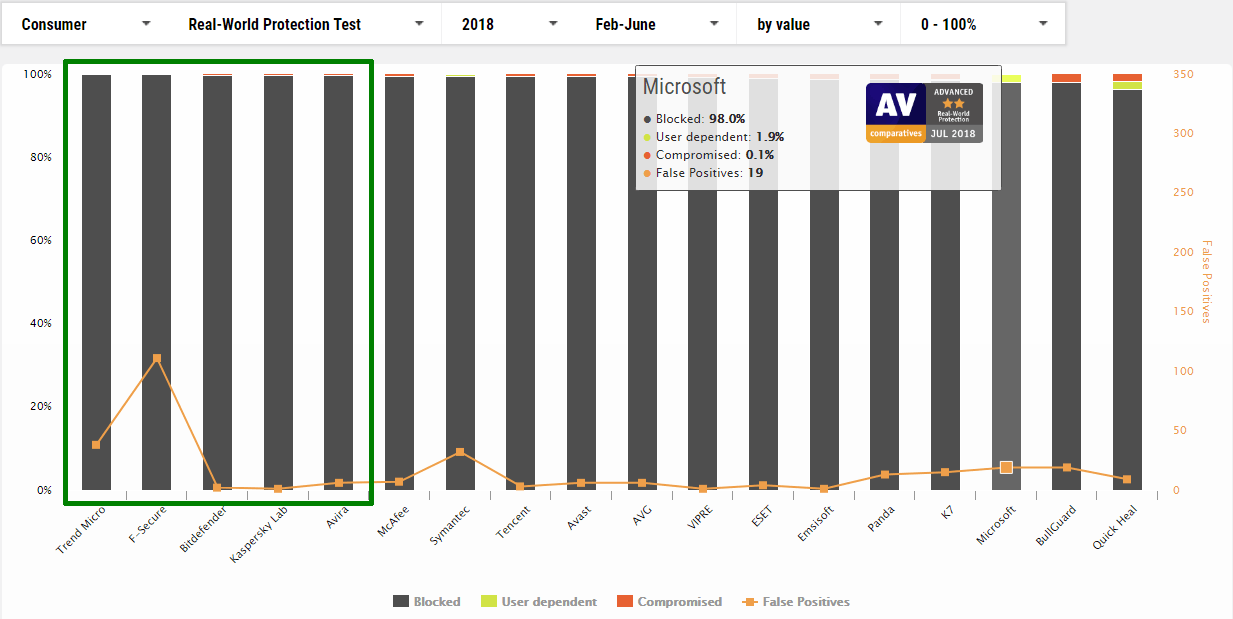
February to June 2018
1 Trend Micro
2 F-Secure
3 Bitdefender
4 Kaspersky Lab
5 Avira
16 Microsoft
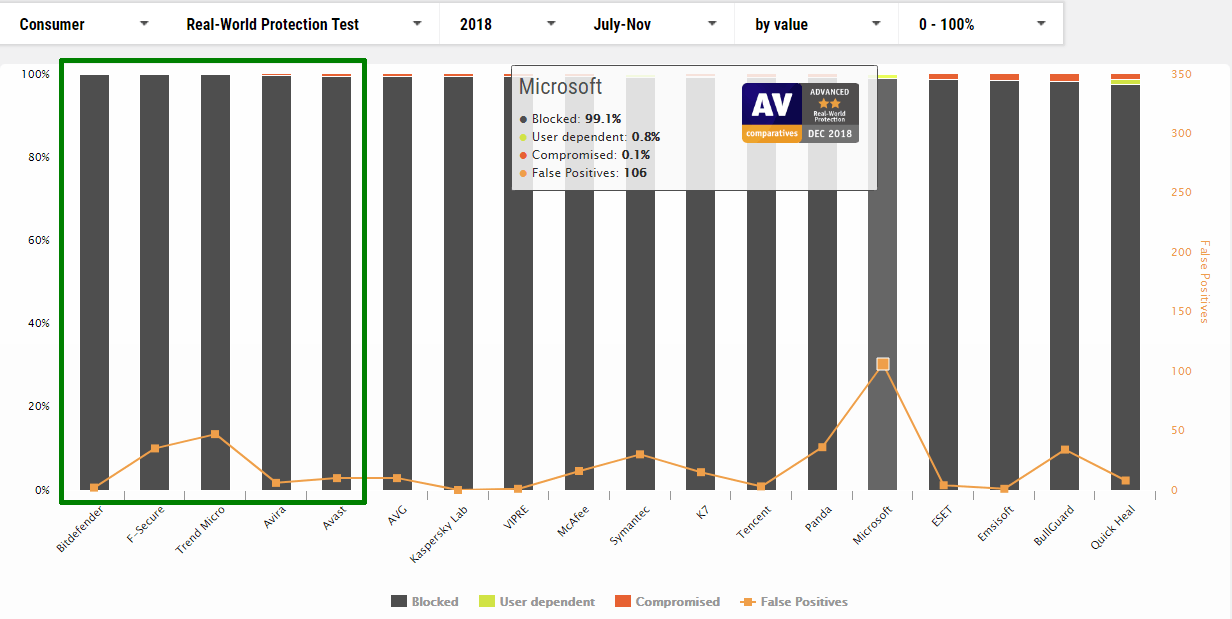
July to November
1 Bitdefender
2 F-Secure
3 Trend Micro
4 Avira
5 Avast
14 Microsoft
Individual months
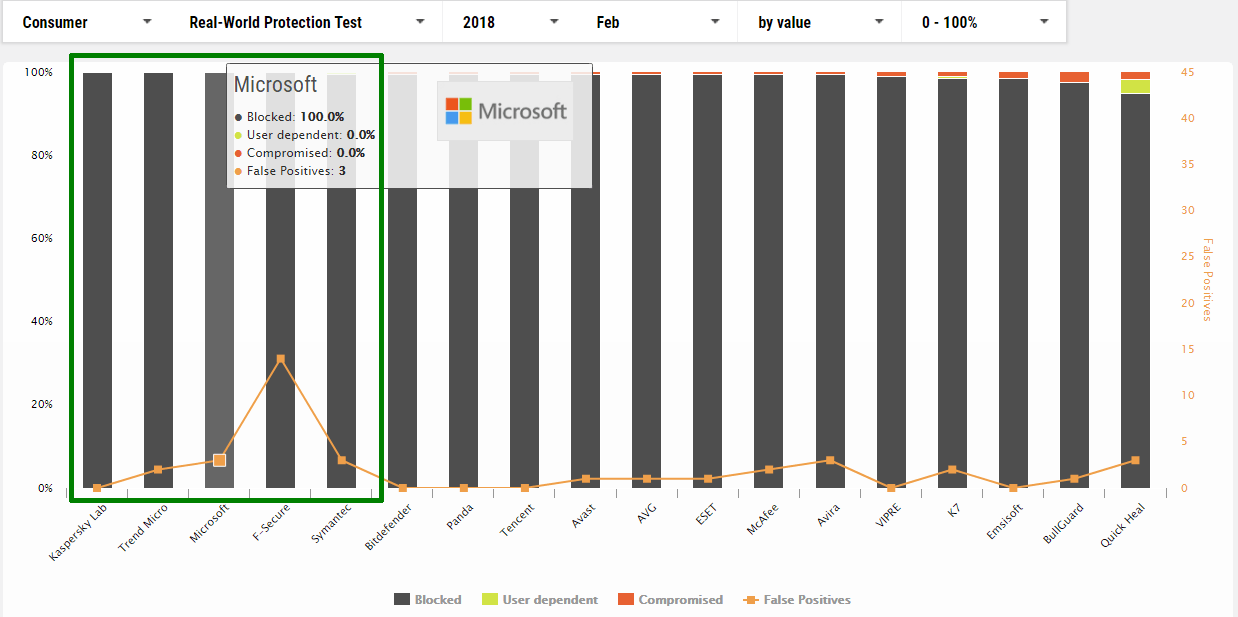
February
1 Kaspersky
2 Trend Micro
3 Microsoft
4 F-Secure *
5 Symantec
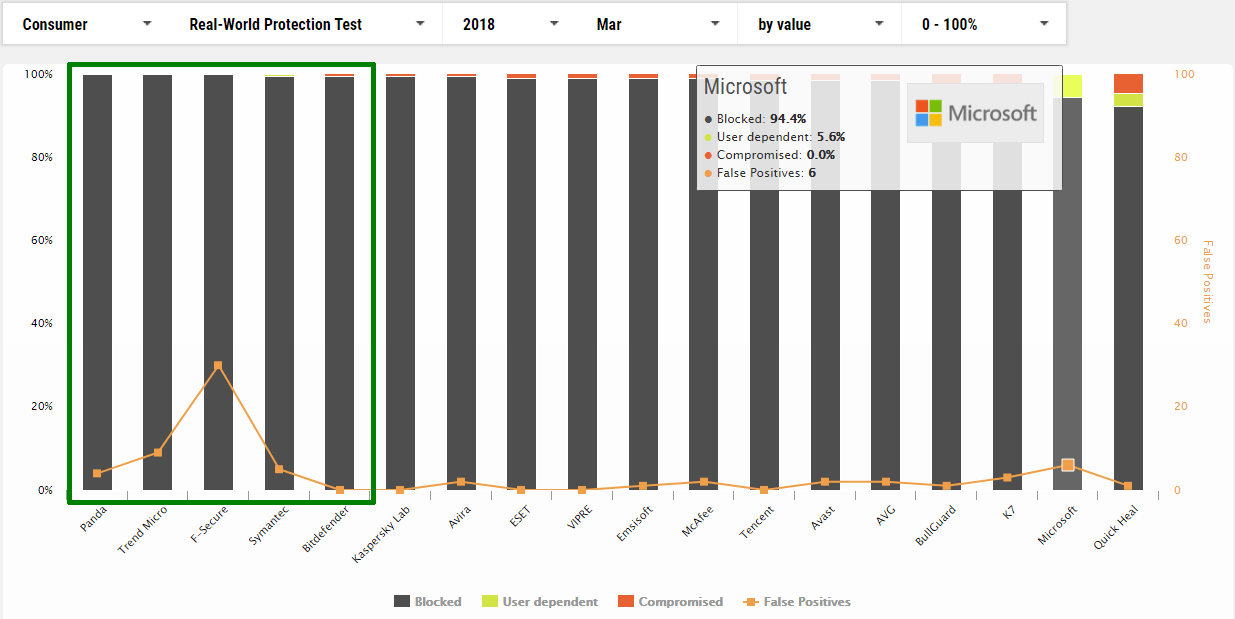
March
1 Panda
2 Trend Micro
3 F-Secure *
4 Symantec
5 Bitdefender
17 Microsoft
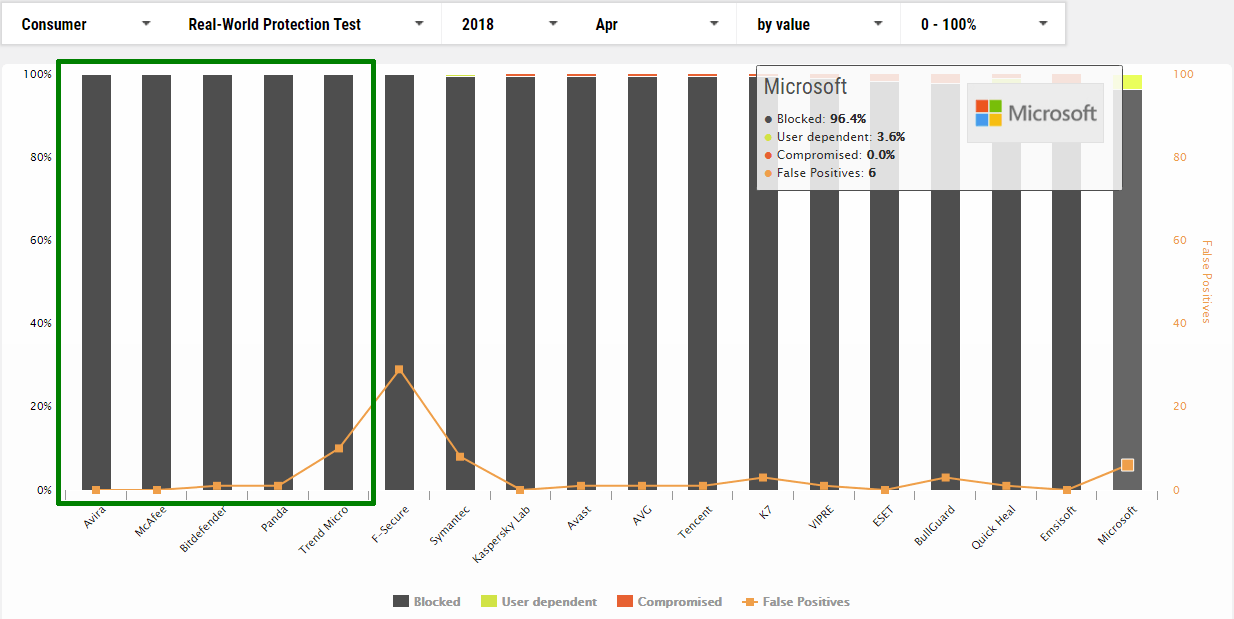
April
1 Avira
2 McAfee
3 Bitdefender
4 Panda
5 Trend Micro
18 Microsoft
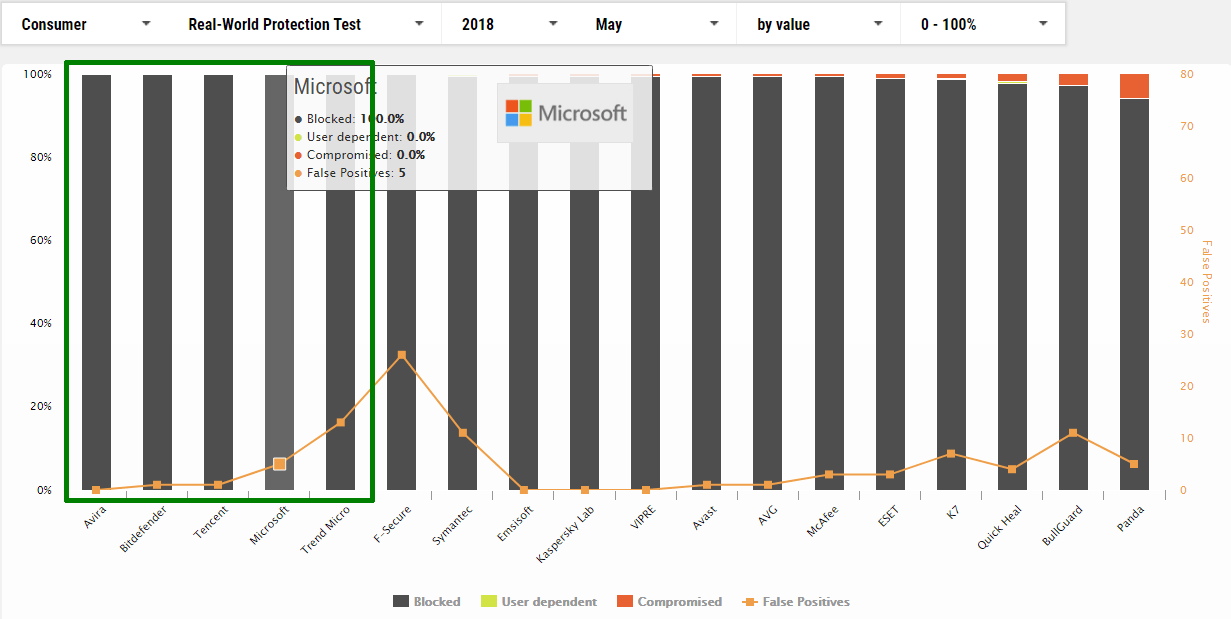
May
1 Avira
2 Bitdefender
3 Tencent
4 Microsoft
5 Trend Micro
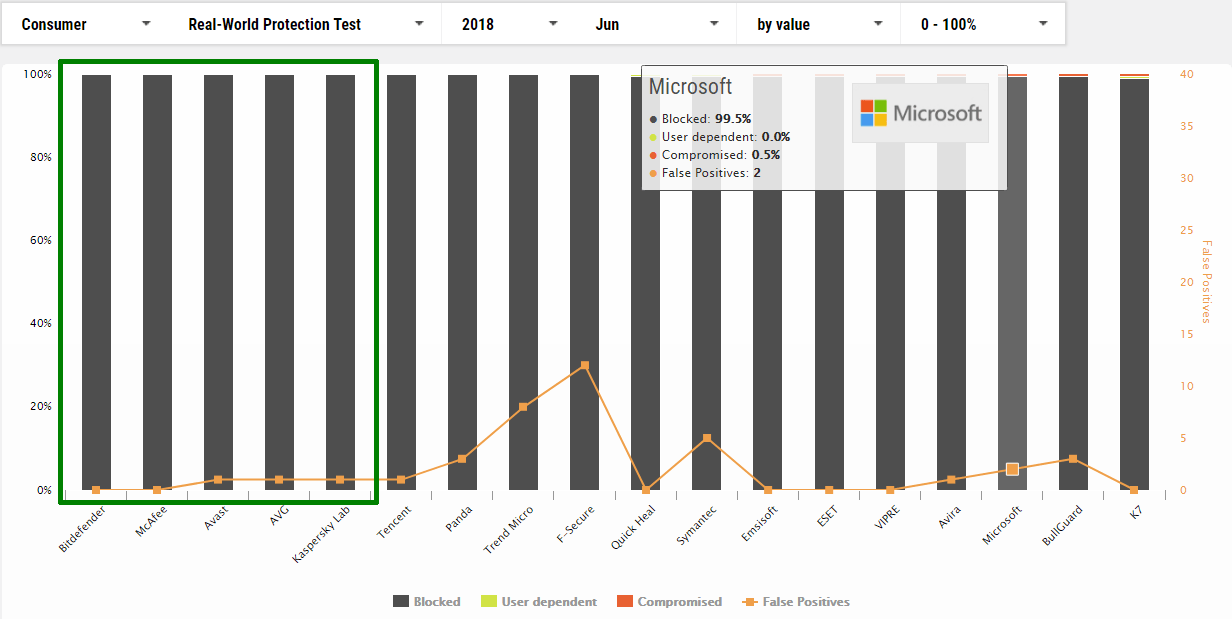
June
1 Bitdefender
2 McAfee
3 Avast
4 AVG
5 Kaspersky
16 Microsoft
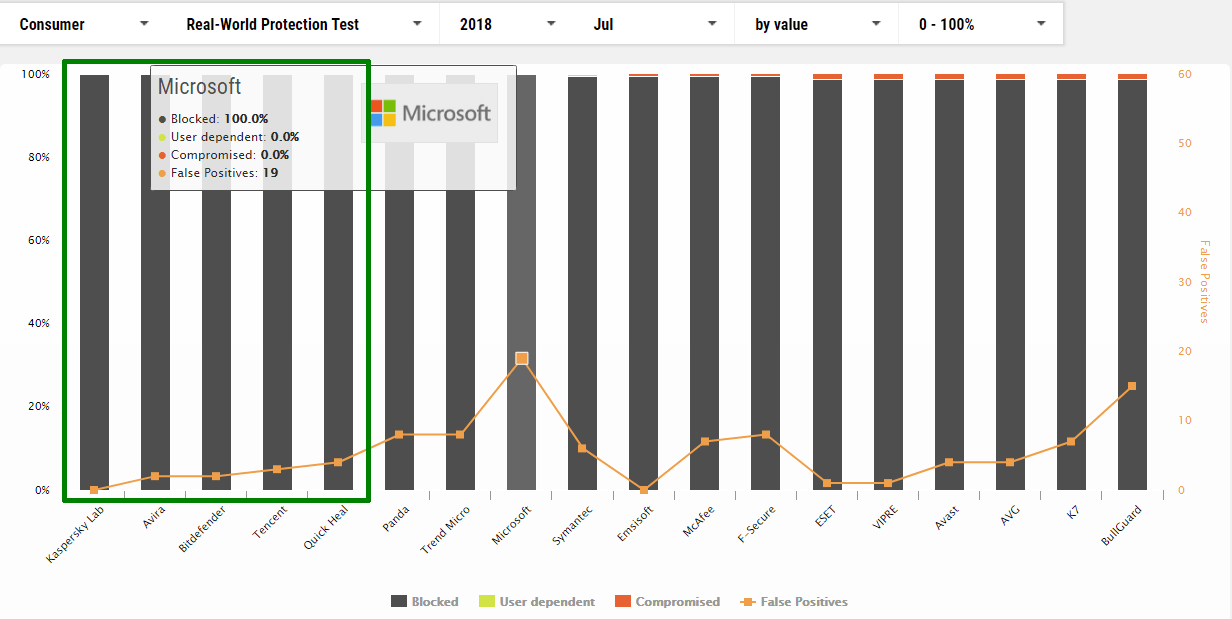
July
1 Kaspersky
2 Avira
3 Bitdefender
4 Tencent
5 Quick Heal
8 Microsoft *
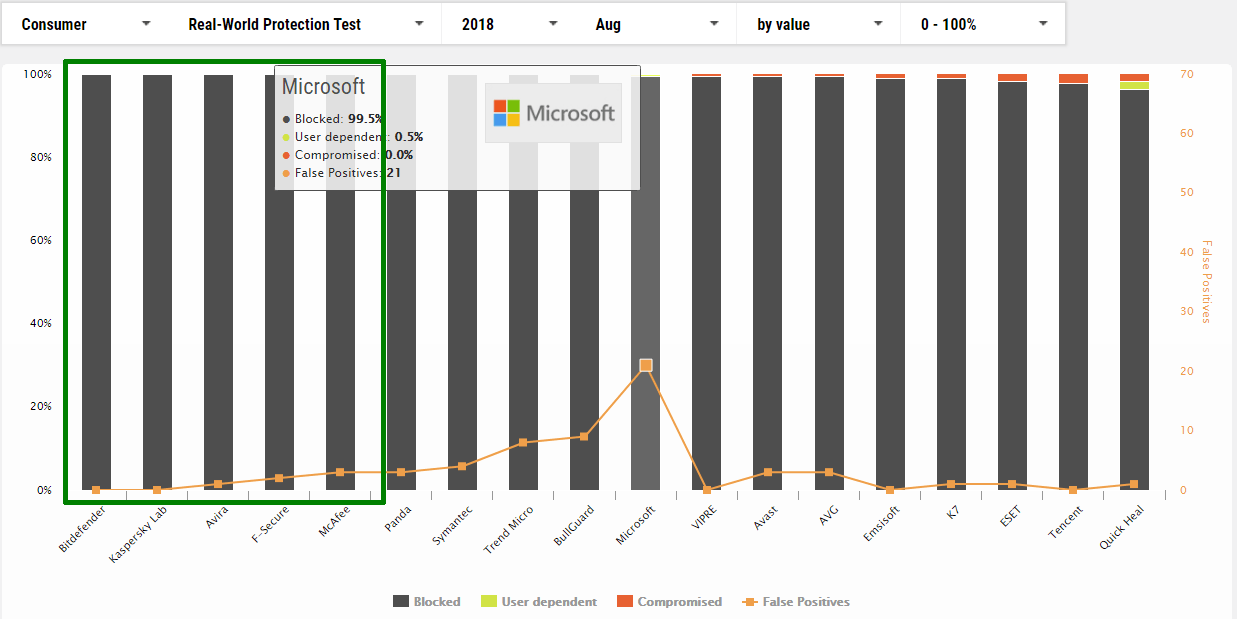
August
1 Bitdefender
2 Kaspersky
3 Avira
4 F-Secure
5 McAfee
10 Microsoft *
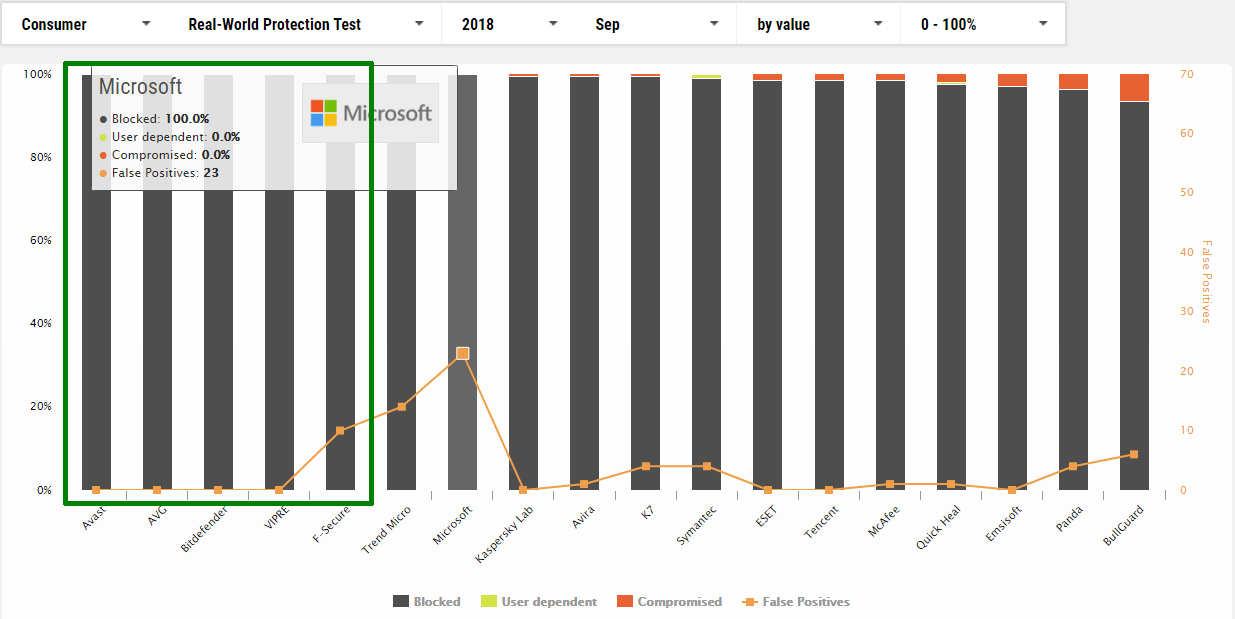
September
1 Avast
2 AVG
3 Bitdefender
4 VIPRE
5 F-Secure
7 Microsoft *
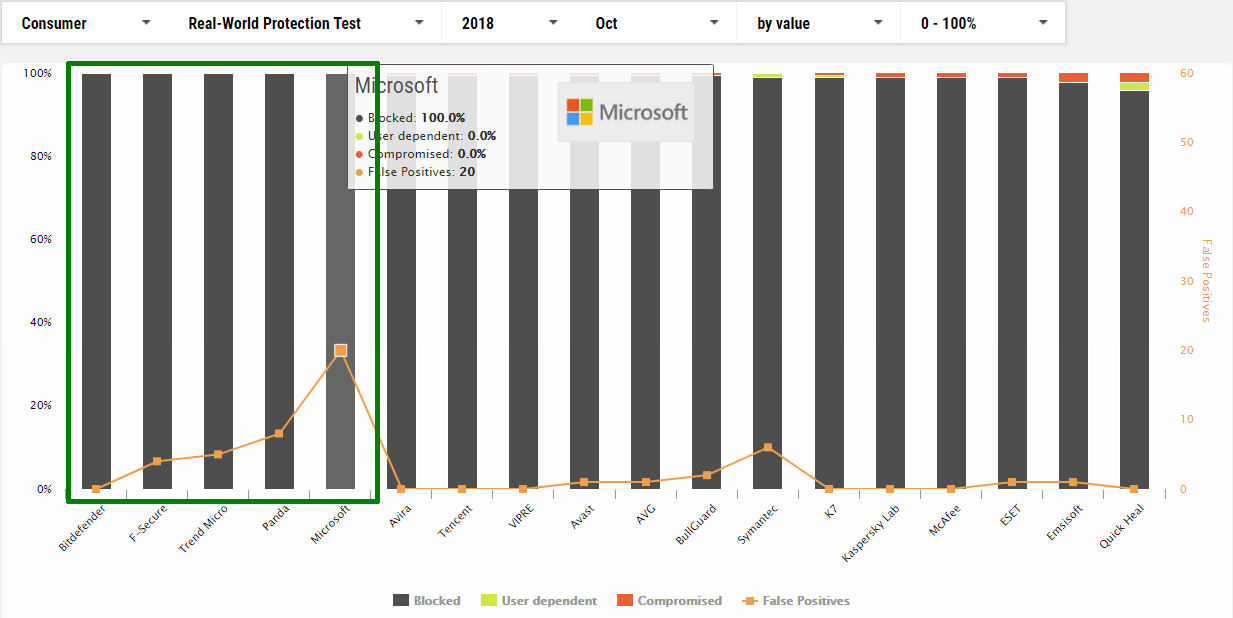
October
1 Bitdefender
2 F-Secure
3 Trend Micro
4 Panda
5 Microsoft *
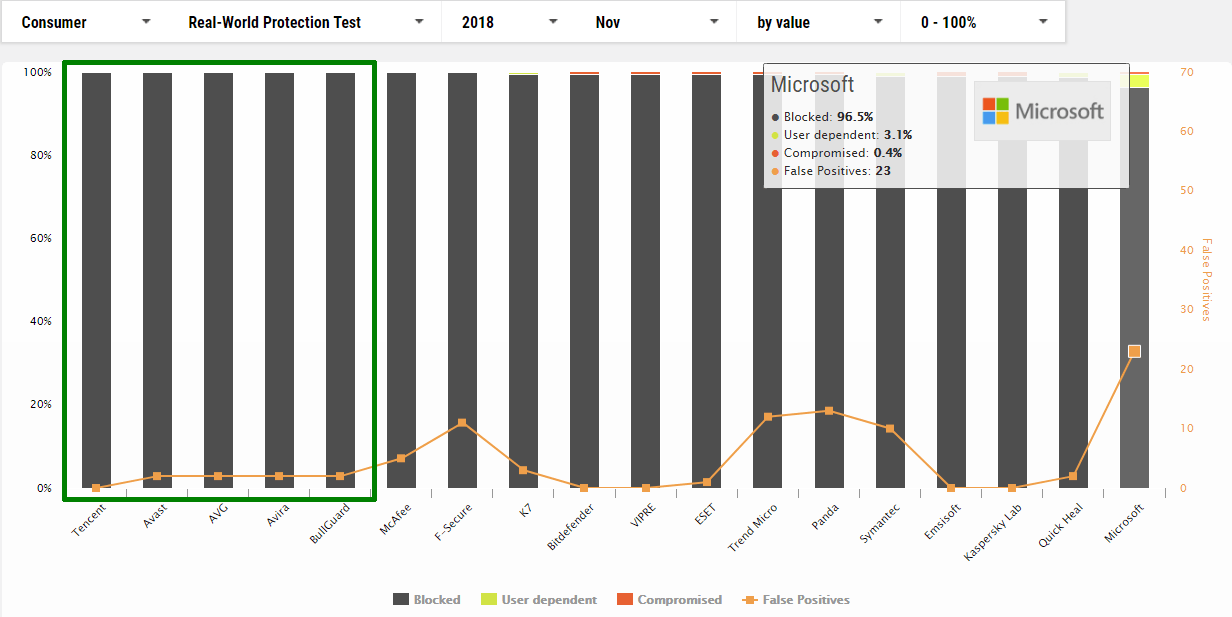
November
1 Tencent
2 Avast
3 AVG
4 Avira
5 BullGuard
18 Microsoft *
Final Analysis and Context
Months in the top 5
Bitdefender x8
Avira x5
F-Secure x5
Trend Micro x5
Kaspersky x4
Avast x3
AVG x3
McAfee x3
Microsoft x3
Panda x3
Tencent x3
BullGuard x1
Quick Heal x1
VIPRE x1
Highest false positives
F-Secure x5
Microsoft x5

Microsoft (the baseline) are rarely in the top 5 in any year, and are mostly near the bottom.
Last year they managed 3 months in the top 5, coming equal with Avast, AVG, McAfee, Panda and Tencent.
Microsoft share the most amount of false positives with F-Secure at 5 months each.
Both out-do the consistently worst performing AV on this score, however F-Secure is also in the top 5 for an equal amount of time.
Avira, F-Secure and Trend Micro all spent 5 months in the top 5, but all showed occasional big swings in reliability, however they most of the time stayed in the top half even when not in the top 5.
Kaspersky may only have been in the top 5 for 4 months, but only twice dropped to the bottom half, and consistently stayed near the top.
There is a clear winner here, and that has to be Bitdefender, which yet again stayed in the top 5 longer than any other with an impressive 8 months, and always with a low false positive rate.
Short recommendations:
If you want to pay, buy Bitdefender. (the free version is very limited)
If you want free, also consider Avira and Kaspersky Lab
If you want a lucky 8-ball, use Microsoft
Comment and criticism of this post in the forums
https://forum.vivaldi.net/topic/34007/2018-av-comparison

5 comments Write a comment