As we seem to be eternally blue about the Windows network access vulnerabilities, and the latest botnet threat, I thought before I take cover I will have a look over the battlefield.
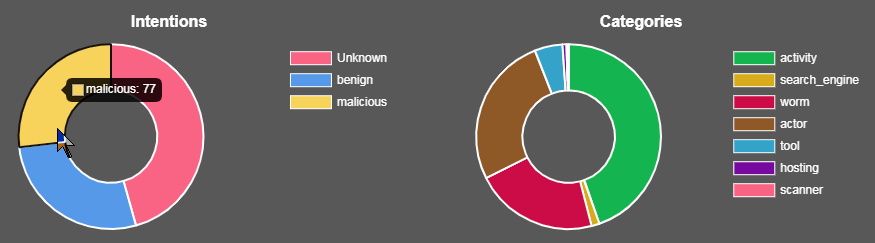
Spotting the new GoldBrute botnet is not as easy as with other activity so I thought I would look at related activity and current big spikes, seen by the GreyNoise site to see if there is a correlation https://viz.greynoise.io/stats
I looked at the common exploits and scanners that obviously relate to GoldBrute, SMB, RDP, EternalBlue and BlueKeep. Most show what appears to unusually large daily counts over the past few weeks. There are other filters that you may find also show correlations.
All slides captured on 12th June 2019
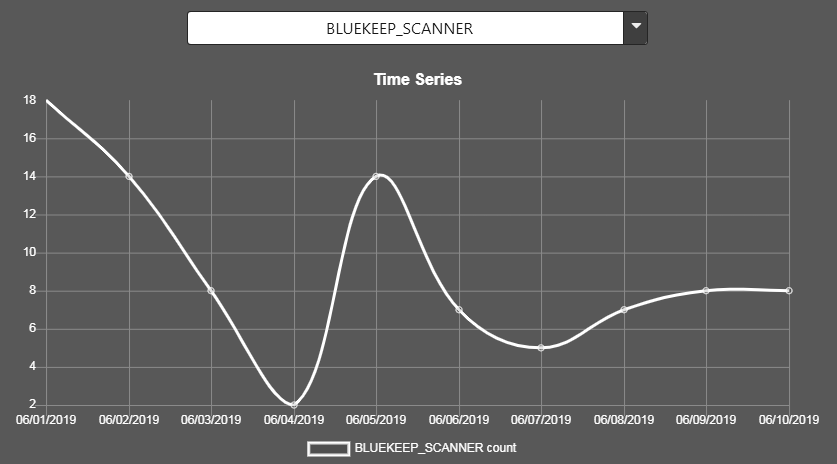
BlueKeep is thankfully not yet on the radar other than a few scans.
The EternalBlue SMB exploit has seen a recent surge in “popularity” even though the patch has been available for over two years.
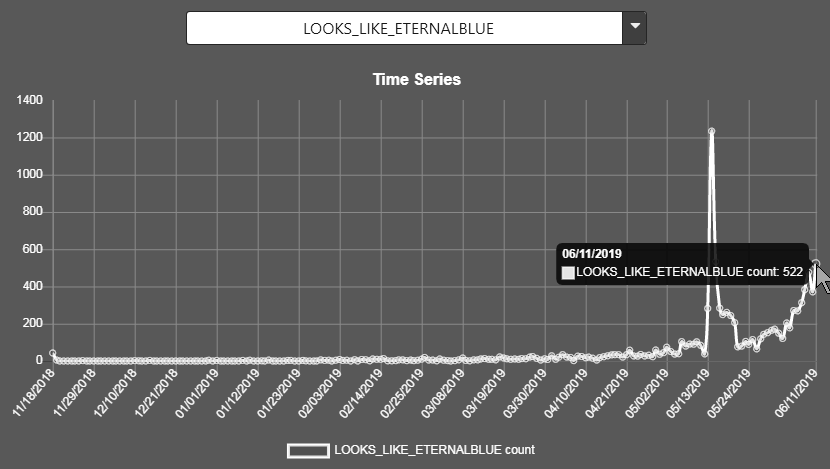
LOOKS_LIKE_ETERNALBLUE (Peaked at 1234 on the 5th of May then dropped to normal, but now accelerating fast)
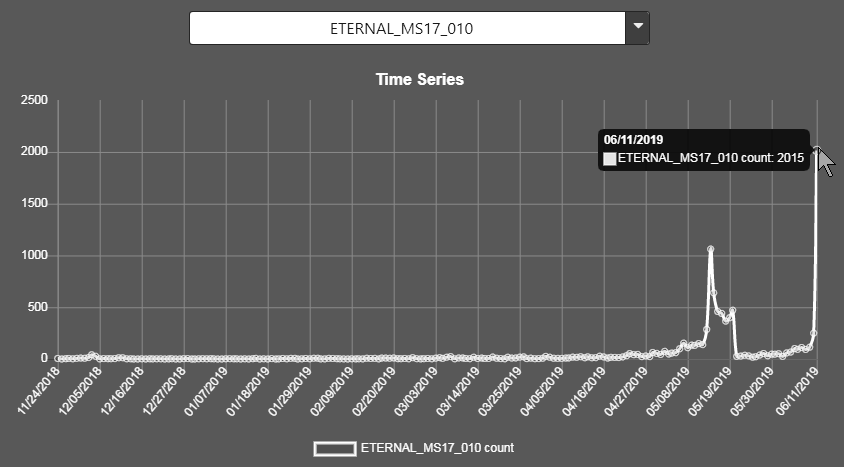
ETERNAL_MS17_010 (Saw a big spike on the 14th of May at 1062 and dropped off. Now leapt to 2015 per day)
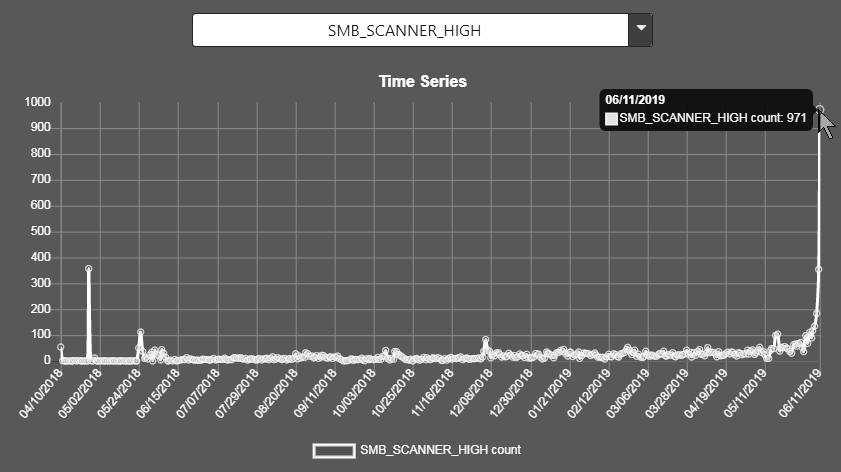
SMB_SCANNER_HIGH (jumped to 971 per day. Previous peak was 357 on the 26th of April last year)
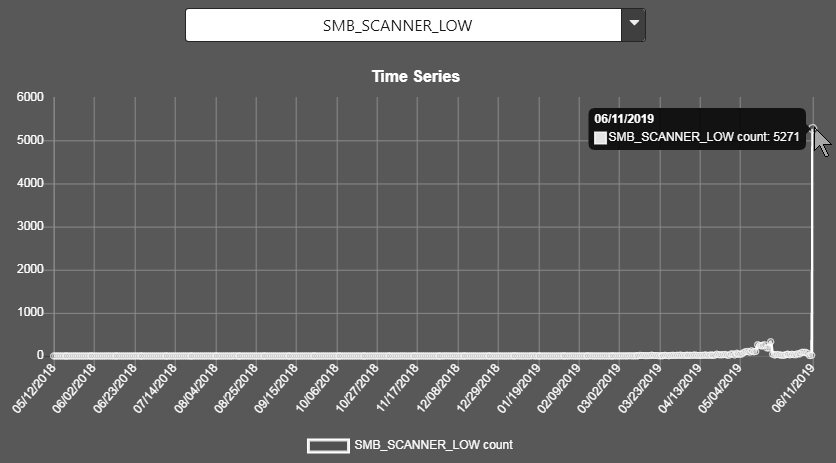
SMB_SCANNER_LOW (just jumped through the roof at 5271 per day. Previous peak over the past year 330 per day on the 20th of May)
OK what about RDP exploits and scans. If we can’t see dynamic info on the GoldBrute activity, what is happening in parallel ?
MASSCAN_CLIENT (This is the client made by Robert Graham) shows normal activity and no recent spikes.
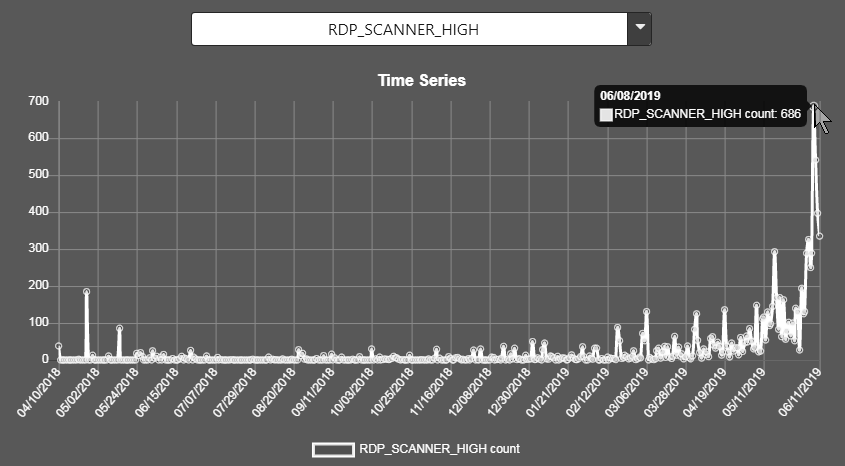
RDP_SCANNER_HIGH (peaked on the 8th of June at 686 per day, now at half that)
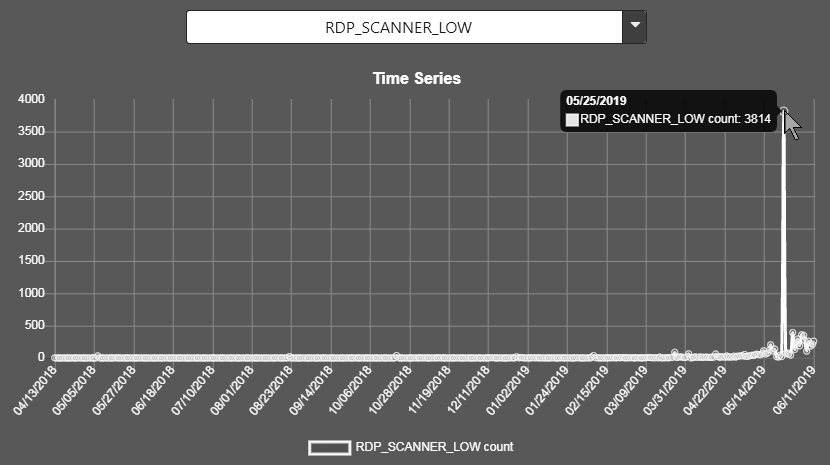
RDP_SCANNER_LOW (Big spike on the 25th of May at 3814 per day. Now at normal of between 200 to 300. I see using the map there has been activity in the Reykjavik area).
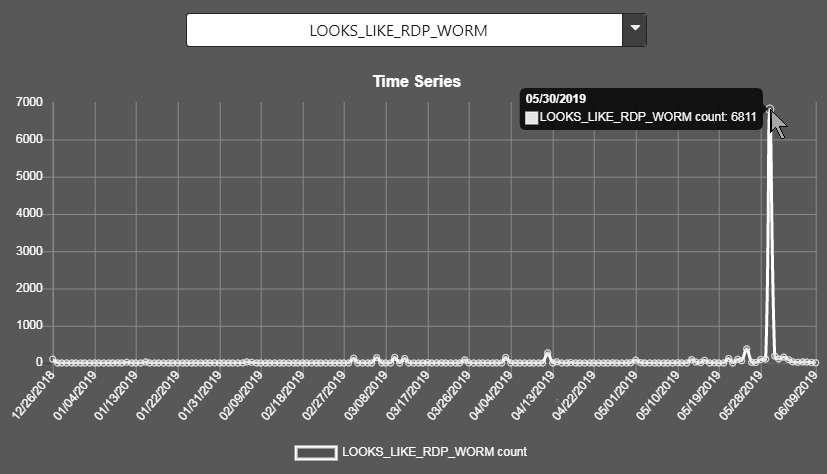
LOOKS_LIKE_RDP_WORM (huge spike on the 30th of May at 6811 per day then dropped back to single and double figures)
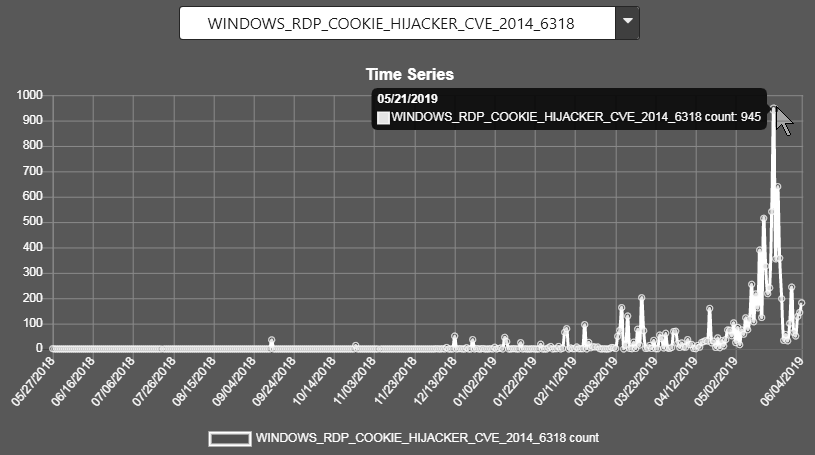
WINDOWS_RDP_COOKIE_HIJACKER_CVE_2014_6318 (biggest spike on the 21st of May at 945 per day now back to recent elevated levels)
Do we have any other dramatic peaks at the same time ?
Slightly.
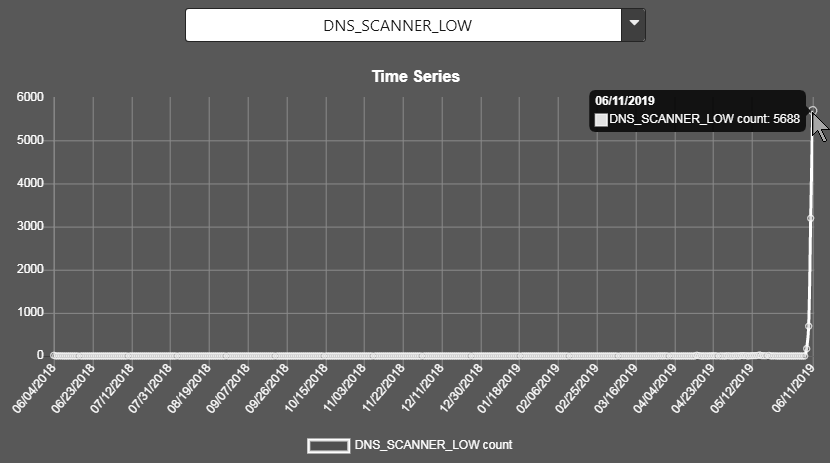
DNS_SCANNER_LOW (been low for over a year, now jumped to 5688 per day)
THOUGHTS
Bare in mind that if you also lookup the MIRAI exploit in the GreyNoise stats you will also see a very recent, very large, very worrying spike, so I am not going to worry about this acorn falling on my head until I see the BLUEKEEP_EXPLOIT fall from the tree.
However,that acorn is very ripe and the wind is picking up, so if you don’t mind, I will be heading inside, where I will curl up in a ball and rock myself to sleep.
When it happens someone else can go and tell the King the sky is falling.
Further reading https://www.shodan.io/search?query=Remote+desktop
https://forum.vivaldi.net/topic/37988/the-internet-was-fun-while-it-lasted-rise-of-the-goldbrute-botnet