

Recently Mozilla decided their testing of DoH with Cloudflare is now ready for regular users and it can be enabled for those that want it.
Are you feeling jealous of your Firefox friends and DNS over HTTPS ?
Don’t worry Cinderella you can go to the ball.
IMPORTANT NOTES: Bypassing the system DNS with the browser will also bypass the HOSTS file, so you need alternative blocking (which this blog also covers).
Chrome does not yet support Encrypted SNI
Unfortunately using DNS over HTTPS is not as simple as changing your DNS in your computer or device, due to it needing to deal with the extra authentication.
The current standard Operating System DNS system does not have this capability, so you need a replacement DNS service or a client to handle the authentication of the keys used by the DNS resolvers.
The easiest solution is to use DNSCrypt Proxy as a replacement DNS service for your computer, router, phone or pi-hole.
There is some confusion with people comparing DoH to DNSCrypt.
This is understandable if you read the out-dated info on the Cisco site for the original version.
However DNSCrypt 2 is much more than a DNS service with encryption.
DNSCrypt is not actually a straight alternative. It already used DNS over TLS (which is preferable for many users), and now has DoH as an already enabled option if you use Simple DNSCrypt.
It also does not break DNSSec (out-dated Cisco info) and Simple DNSCrypt actually gives you the option to only use DNSSec resolvers by default.
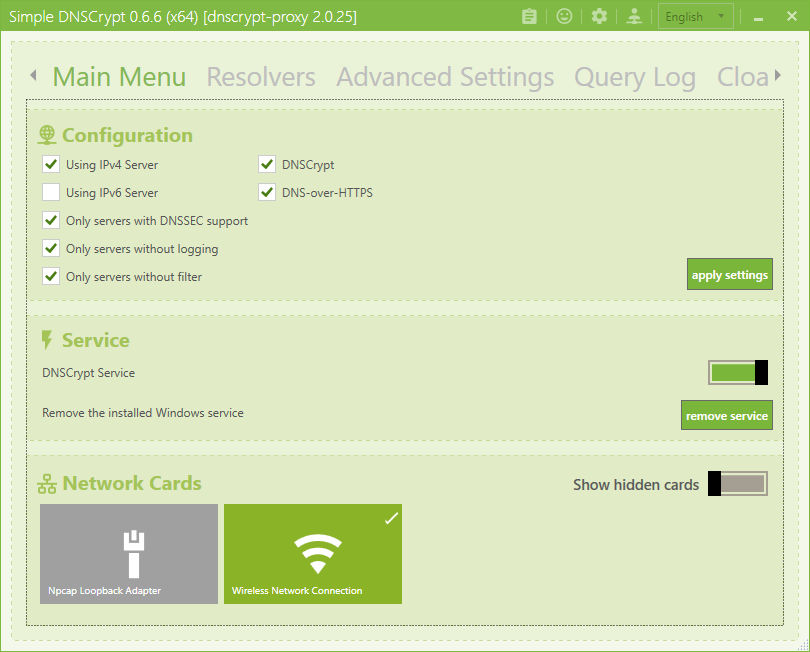
I know it does work with DNSSec for sure, as while the TLS/DANE validation extension still worked, it worked as it should.
If you actually want to trust DNSSec it also requires that the sites you use have configured it (most have not)
https://dnssec-name-and-shame.com/domain/accounts.google.com
https://dnssec-name-and-shame.com/domain/login.live.com
https://dnssec-name-and-shame.com/domain/login.vivaldi.net
Cloudflare and Quad9 also use DNScrypt as well as DoH.
Many DNSCrypt users tend not to use official Cisco OpenDNS because they log, so are not considered private.
https://dnscrypt.info/public-servers/
DNSCrypt mainly differs in use to other DNS services in that you have locally stored keys so the client can authenticate the resolver.
Encryption is all well and good, but just the same as HTTPS, without a way to do key exchanges and authentication it leaves Man-in-the-middle interference as possible. That is the extra armour that DNSCrypt gives you as a replacement DNS service.
If you install Simple DNSCrypt you will see the default is DoH on, and to only list DNSSec, non-logging, non-filtered resolvers.
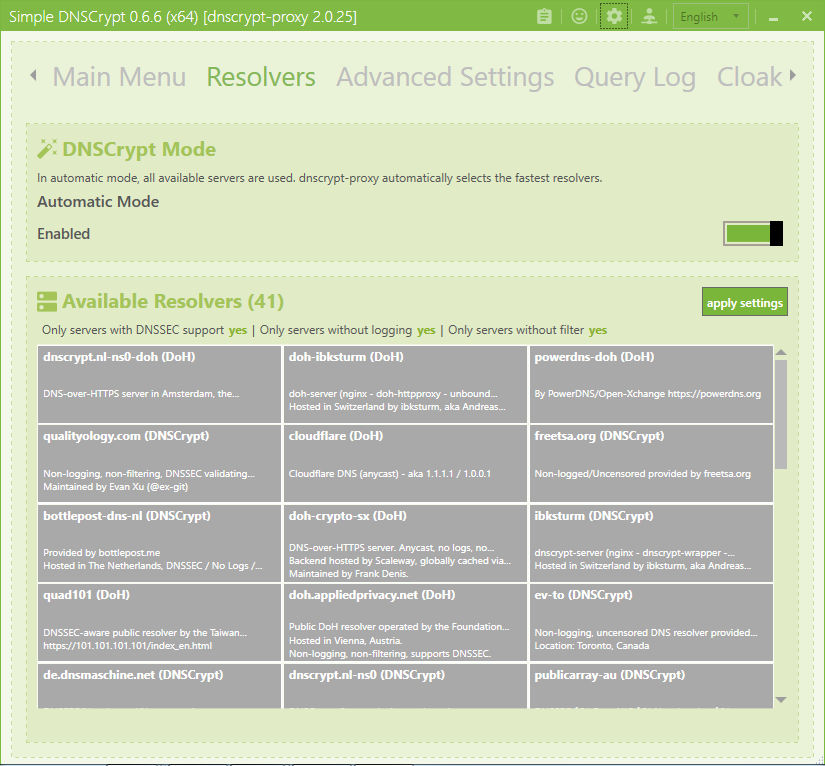
It then uses whichever is the fastest responding from the filtered list. You can watch the live lookups in the logging tab to see which resolver is fetching what IP.
OK. so you like to stick with cloudflare or Quad9 etc.
Disable auto mode and find the cloudflare and/or Quad9 resolvers in the list (to show the Quad9 DNS you have to show DNS that filter). You can select one or both, or as many others you also feel you trust or are closest.
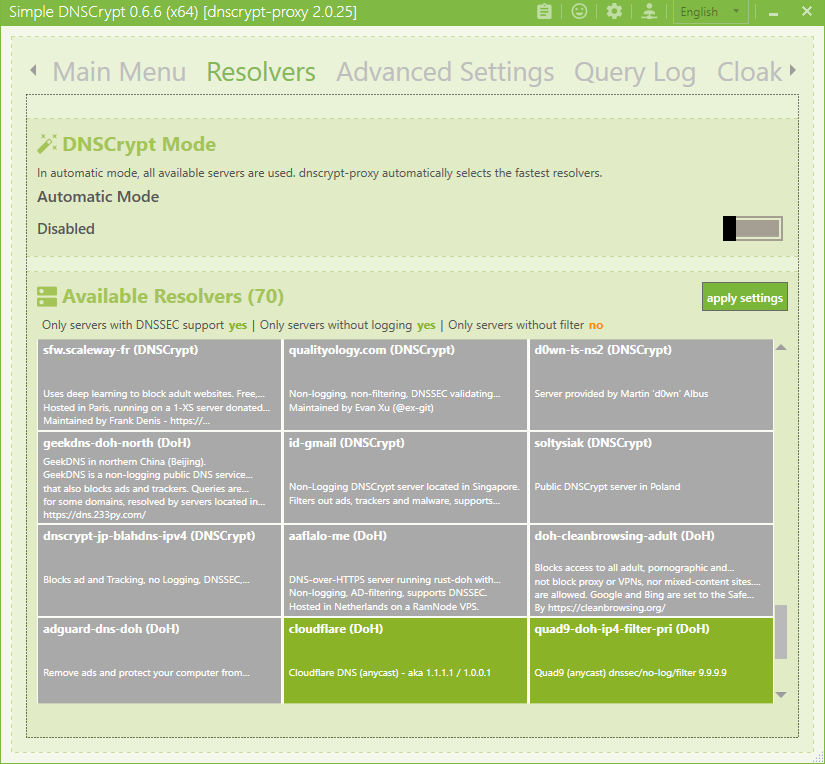
Again it will now use whichever is fastest.
It falls back to basic Quad9 access if for some reason it cannot use one with DNSCrypt (this can be changed).
It also lets you swap from UDP to TCP so will support TOR.
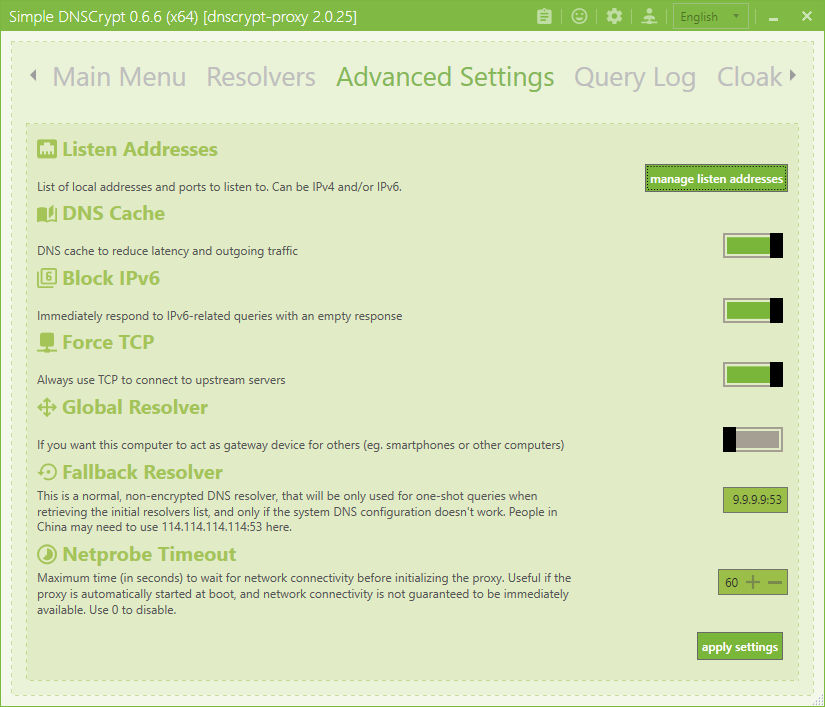
For blocking you can import public blacklists or maintain your own.
For people that want a “HOSTS on steroids” you can use the Cloak and Forward feature.
Why just have DoH in 1 browser, when your OS or flashable router can use it and therefore any other browser or software you use ?
Yeah it means you install some extra software, but without a replacement DNS service the OS cannot handle authenticated DNS like browsers can (when they try).
Features
- DNS traffic encryption and authentication. Supports DNS-over-HTTPS (DoH) using TLS 1.3, and DNSCrypt.
- DNS query monitoring, with separate log files for regular and suspicious queries
- Filtering: block ads, malware, and other unwanted content. Compatible with all DNS services
- Time-based filtering, with a flexible weekly schedule
- Transparent redirection of specific domains to specific resolvers
- DNS caching, to reduce latency and improve privacy
- Local IPv6 blocking to reduce latency on IPv4-only networks
- Load balancing: pick a set of resolvers, dnscrypt-proxy will automatically measure and keep track of their speed, and balance the traffic across the fastest available ones.
- Cloaking: like a
HOSTSfile on steroids, that can return preconfigured addresses for specific names, or resolve and return the IP address of other names. This can be used for local development as well as to enforce safe search results on Google, Yahoo and Bing. - Automatic background updates of resolvers lists
- Can force outgoing connections to use TCP
- Supports SOCKS proxies
- Compatible with DNSSEC
The wiki has installation info for;
- Windows
- macOS
- Linux
- pfsense
- pi-hole
- OpenWRT / LEDE
- Synology
- OPNsense
Up-to-date, pre-built binaries are available for:
- Android/arm
- Android/arm64
- Android/x86
- Android/x86_64
- Dragonfly BSD
- FreeBSD/arm
- FreeBSD/x86
- FreeBSD/x86_64
- Linux/arm
- Linux/arm64
- Linux/mips
- Linux/mipsle
- Linux/mips64
- Linux/mips64le
- Linux/x86
- Linux/x86_64
- MacOS X
- NetBSD/x86
- NetBSD/x86_64
- OpenBSD/x86
- OpenBSD/x86_64
- Windows
- Windows 64 bit
Prebuilt Installers
https://dnscrypt.info/implementations
https://github.com/jedisct1/dnscrypt-proxy/wiki/Installation#graphical-front-ends
How to test DoH is working
Make sure you have disabled DNSCrypt protocol and only have DNS-over-HTTPS enabled.
Select only Cloudflare as a single resolver and visit https://1.1.1.1/help
This will test for DoH and DoT over ip4 and ip6
If it shows as working you can enable the rest of the resolvers you want or go back to automatic mode.
You can also use the ESNI test page which also checks your DNS for DNSSEC and TLS1.3
https://www.cloudflare.com/ssl/encrypted-sni/
 CHROMIUM
CHROMIUM
DoH in chrome has been available since last year, but apparently they have not enabled it due to, “there is this thing we want to do with the UI but it needs a thing and we have other things to do”.
All it needs is a switch. A tick does not constitute a crisis of GUI and massive delay.
To force DoH using Cloudflare in Chrome you have to launch with extra command line parameters.
You can either make a batch file or edit the properties of the icon you use to run the browser (paste the following in the “Target” box in the icon properties).
chrome.exe --enable-features="dns-over-https<DoHTrial" --force-fieldtrials="DoHTrial/Group1" --force-fieldtrial-params="DoHTrial.Group1:server/https%3A%2F%2F1.1.1.1%2Fdns-query/method/POST
Change the “chrome.exe” for the name of the Chromium browser you are using.
